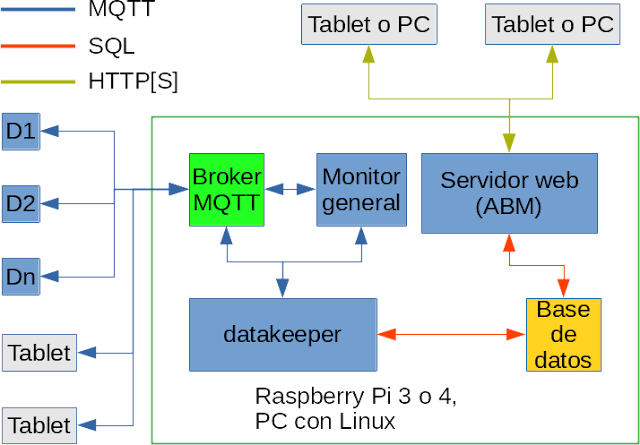
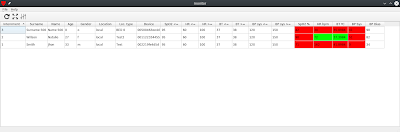
Review:
Lower Ed, by Tressie McMillan Cottom
| Publisher: |
The New Press |
| Copyright: |
2017 |
| Printing: |
2018 |
| ISBN: |
1-62097-472-X |
| Format: |
Kindle |
| Pages: |
217 |
Lower Ed (subtitled
The Troubling Rise of For-Profit Colleges
in the New Economy) is the first book by sociologist Tressie McMillan
Cottom. (I previously reviewed her second book, the excellent essay
collection
Thick.) It is a deep look at
the sociology of for-profit higher education in the United States based on
interviews with students and executives, analysis of Wall Street filings,
tests of the admissions process, and her own personal experiences working
for two of the schools. One of the questions that McMillan Cottom tries
to answer is why students choose to enroll in these institutions,
particularly the newer type of institution funded by federal student loans
and notorious for being more expensive and less valuable than non-profit
colleges and universities.
I was hesitant to read this book because I find for-profit schools
depressing. I grew up with the ubiquitous commercials, watched the
backlash develop, and have a strongly negative impression of the industry,
partly influenced by having worked in traditional non-profit higher
education for two decades. The prevailing opinion in my social group is
that they're a con job. I was half-expecting a reinforcement of that
opinion by example, and I don't like reading infuriating stories about
people being defrauded.
I need not have worried. This is not that sort of book (nor, in
retrospect, do I think McMillan Cottom would approach a topic from that
angle). Sociology is broader than reporting.
Lower Ed positions
for-profit colleges within a larger social structure of education,
credentialing, and changes in workplace expectations; takes a deep look at
why they are attractive to their students; and humanizes and complicates
the motives and incentives of everyone involved, including administrators
and employees of for-profit colleges as well as the students. McMillan
Cottom does of course talk about the profit motive and the deceptions
surrounding that, but the context is less that of fraud that people are
unable to see through and more a balancing of the drawbacks of a set of
poor choices embedded in institutional failures.
One of my metrics for a good non-fiction book is whether it introduces me
to a new idea that changes how I analyze the world.
Lower Ed does
that twice.
The first idea is the view of higher education through the lens of risk
shifting. It used to be common for employers to hire people without prior
job-specific training and do the training in-house, possibly through an
apprenticeship structure. More notably, once one was employed by a
particular company, the company routinely arranged or provided ongoing
training. This went hand-in-hand with a workplace culture of long tenure,
internal promotion, attempts to avoid layoffs, and some degree of mutual
loyalty. Companies expected to invest significantly in an employee over
their career and thus also had an incentive to retain that employee rather
than train someone for a competitor.
However, from a purely financial perspective, this is a risk and an
inefficiency, similar to the risk of carrying a large inventory of parts
and components. Companies have responded to investor-driven focus on
profits and efficiency by reducing overhead and shifting risk. This leads
to the lean supply chain, where no one pays for parts to sit around in
warehouses and companies aren't caught with large stockpiles of
now-useless components, but which is more sensitive to any disruption
(such as from a global pandemic). And, for employment, it leads to a
desire to hire pre-trained workers, retain only enough workers to do the
current amount of work, and replace them with new workers who already have
appropriate training rather than retrain them.
The effect of the corporate decision to only hire pre-trained employees is
to shift the risk and expense of training from the company to the
prospective employee. The individual has to seek out training at their
own expense in the hope (not guarantee) that at the conclusion of that
training they will get or retain a job. People therefore turn to higher
education to both provide that training and to help them decide what type
of training will eventually be valuable. This has a long history with
certain professional fields (doctors and lawyers, for example), but the
requirements for completing training in those fields are relatively clear
(a professional license to practice) and the compensation reflects the
risk. What's new is the shift of training risk to the individual in more
mundane jobs, without any corresponding increase in compensation.
This, McMillan Cottom explains, is the background for the growth in demand
for higher education in general and the the type of education offered by
for-profit colleges in particular. Workers who in previous eras would be
trained by their employers are now responsible for their own training.
That training is no longer judged by the standards of a specific
workplace, but is instead evaluated by a hiring process that expects
constant job-shifting. This leads to increased demand by both workers and
employers for credentials: some simple-to-check certificate of completion
of training that says that this person has the skills to immediately start
doing some job. It also leads to a demand for more flexible class hours,
since the student is now often someone older with a job and a family to
balance. Their ongoing training used to be considered a cost of business
and happen during their work hours; now it is something they have to fit
around the contours of their life because their employer has shifted that
risk to them.
The risk-shifting frame makes sense of the "investment" language so common
in for-profit education. In this job economy, education as investment is
not a weird metaphor for the classic benefits of a liberal arts education:
broadened perspective, deeper grounding in philosophy and ethics, or
heightened aesthetic appreciation. It's an investment in the literal
financial sense; it is money that you spend now in order to get a
financial benefit (a job) in the future. People have to invest in their
own training because employers are no longer doing so, but still require
the outcome of that investment. And, worse, it's primarily a
station-keeping investment. Rather than an optional expenditure that
could reap greater benefits later, it's a mandatory expenditure to
prevent, at best, stagnation in a job paying poverty wages, and at worst
the disaster of unemployment.
This explains renewed demand for higher education, but why for-profit
colleges? We know they cost more and have a worse reputation (and
therefore their credentials have less value) than traditional non-profit
colleges. Flexible hours and class scheduling explains some of this but
not all of it. That leads to the second perspective-shifting idea I got
from
Lower Ed: for-profit colleges are very good at what they focus
time and resources on, and they focus on enrolling students.
It is hard to enroll in a university! More precisely, enrolling in a
university requires bureaucracy navigation skills, and those skills are
class-coded. The people who need them the most are the least likely to
have them.
Universities do not reach out to you, nor do they guide you through the
process. You have to go to them and discover how to apply, something that
is often made harder by the confusing state of many university web sites.
The language and process is opaque unless other people in your family have
experience with universities and can explain it. There might be someone
you can reach on the phone to ask questions, but they're highly unlikely
to proactively guide you through the remaining steps. It's your
responsibility to understand deadlines, timing, and sequence of
operations, and if you miss any of the steps (due to, for example, the
overscheduled life of someone in need of better education for better job
prospects), the penalty in time and sometimes money can be substantial.
And admission is just the start; navigating financial aid, which most
students will need, is an order of magnitude more daunting. Community
colleges are somewhat easier (and certainly cheaper) than universities,
but still have similar obstacles (and often even worse web sites).
It's easy for people like me, who have long professional expertise with
bureaucracies, family experience with higher education, and a support
network of people to nag me about deadlines, to underestimate this. But
the application experience at a for-profit college is entirely different
in ways far more profound than I had realized. McMillan Cottom documents
this in detail from her own experience working for two different
for-profit colleges and from an experiment where she indicated interest in
multiple for-profit colleges and then stopped responding before signing
admission paperwork. A for-profit college is fully invested in helping a
student both apply and get financial aid, devotes someone to helping them
through that process, does not expect them to understand how to navigate
bureaucracies or decipher forms on their own, does not punish unexpected
delays or missed appointments, and goes to considerable lengths to try to
keep anyone from falling out of the process before they are enrolled.
They do not expect their students to already have the skills that one
learns from working in white-collar jobs or from being surrounded by
people who do. They provide the kind of support that an educational
institution should provide to people who, by definition, don't understand
something and need to learn.
Reading about this was infuriating. Obviously, this effort to help people
enroll is largely for predatory reasons. For-profit schools make their
money off federal loans and they don't get that money unless they can get
someone to enroll and fill out financial paperwork (and to some extent
keep them enrolled), so admissions is their cash cow and they act
accordingly. But that's not why I found it infuriating; that's just
predictable capitalism. What I think is inexcusable is that nothing they
do is that difficult. We could being doing the same thing for prospective
community college students but have made the societal choice not to. We
believe that education is valuable, we constantly advocate that people get
more job training and higher education, and yet we demand prospective
students navigate an unnecessarily baroque and confusing application
process with very little help, and then stereotype and blame them for
failing to do so.
This admission support is not a question of resources. For-profit
colleges are funded almost entirely by federally-guaranteed student loans.
We are paying them to help people apply. It is, in McMillan
Cottom's term, a negative social insurance program. Rather than buffering
people against the negative effects of risk-shifting of employers by
helping them into the least-expensive and most-effective training programs
(non-profit community colleges and universities), we are spending tax
dollars to enrich the shareholders of for-profit colleges while
underfunding the alternatives. We are choosing to create a gap that routes
government support to the institution that provides worse training at
higher cost but is very good at helping people apply. It's as if the
unemployment system required one to use payday lenders to get one's
unemployment check.
There is more in this book I want to talk about, but this review is
already long enough. Suffice it to say that McMillan Cottom's analysis
does not stop with market forces and the admission process, and the parts
of her analysis that touch on my own personal experience as someone with a
somewhat unusual college path ring very true. Speaking as a former
community college student, the discussion of class credit transfer
policies and the way that institutional prestige gatekeeping and the
desire to push back against low-quality instruction becomes a trap that
keeps students in the for-profit system deserves another review this
length. So do the implications of risk-shifting and credentialism on the
morality of "cheating" on schoolwork.
As one would expect from the author of
the essay
"Thick" about bringing context to sociology,
Lower Ed is personal
and grounded. McMillan Cottom doesn't shy away from including her own
experiences and being explicit about her sources and research. This is
backed up by one of the best methodological notes sections I've seen in a
book. One of the things I love about McMillan Cottom's writing is that
it's solidly academic, not in the sense of being opaque or full of jargon
(the text can be a bit dense, but I rarely found it hard to follow), but
in the sense of being clear about the sources of knowledge and her methods
of extrapolation and analysis. She brings her receipts in a refreshingly
concrete way.
I do have a few caveats. First, I had trouble following a structure and
line of reasoning through the whole book. Each individual point is
meticulously argued and supported, but they are not always organized into
a clear progression or framework. That made
Lower Ed feel at times
like a collection of high-quality but somewhat unrelated observations
about credentials, higher education, for-profit colleges, their student
populations, their business models, and their relationships with
non-profit schools.
Second, there are some related topics that McMillan Cottom touches on but
doesn't expand sufficiently for me to be certain I understood them. One
of the big ones is credentialism. This is apparently a hot topic in
sociology and is obviously important to this book, but it's referenced
somewhat glancingly and was not satisfyingly defined (at least for me).
There are a few similar places where I almost but didn't quite follow a
line of reasoning because the book structure didn't lay enough foundation.
Caveats aside, though, this was meaty, thought-provoking, and eye-opening,
and I'm very glad that I read it. This is a topic that I care more about
than most people, but if you have watched for-profit colleges with
distaste but without deep understanding, I highly recommend
Lower
Ed.
Rating: 8 out of 10
 Kubernetes is
Kubernetes is  I had been thinking of doing a blog post on RCEP which China signed with 14 countries a week and a day back but this new story has broken and is being viraled a bit on the interwebs, especially twitter and is pretty much in our domain so thought would be better to do a blog post about it. Also, there is quite a lot packed so quite a bit of unpacking to do.
I had been thinking of doing a blog post on RCEP which China signed with 14 countries a week and a day back but this new story has broken and is being viraled a bit on the interwebs, especially twitter and is pretty much in our domain so thought would be better to do a blog post about it. Also, there is quite a lot packed so quite a bit of unpacking to do.
 Sneakers was much more interesting for me because in that you got the best key which can unlock any lock, something like quantum computing is supposed to do. One could equate both the first movies in either as a White hat or a Grey hat . A Grey hat is more flexible in his/her moral values, and they are plenty of such people. For e.g. Julius Assange could be described as a Grey hat, but as you can see and understand those are moral issues.
Sneakers was much more interesting for me because in that you got the best key which can unlock any lock, something like quantum computing is supposed to do. One could equate both the first movies in either as a White hat or a Grey hat . A Grey hat is more flexible in his/her moral values, and they are plenty of such people. For e.g. Julius Assange could be described as a Grey hat, but as you can see and understand those are moral issues. 
 The Debian project is happy to announce a donation of 10,000 to help
The Debian project is happy to announce a donation of 10,000 to help



 I have been quite absent from Debian stuff lately, but this increased since COVID-19 hits us. In this blog post I'll try to sketch what I have been doing to help fight COVID-19 this last few months.
I have been quite absent from Debian stuff lately, but this increased since COVID-19 hits us. In this blog post I'll try to sketch what I have been doing to help fight COVID-19 this last few months.